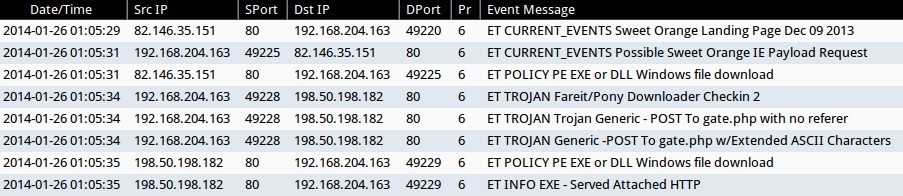
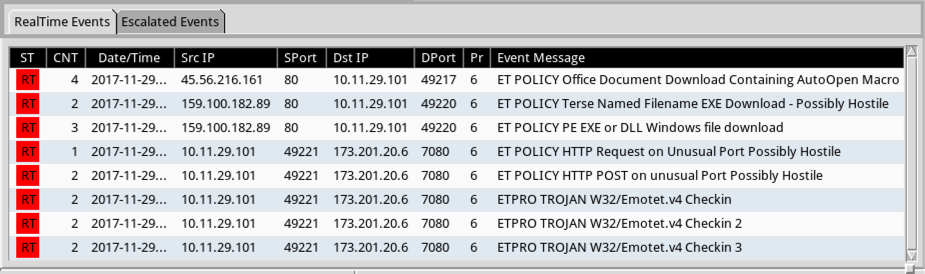
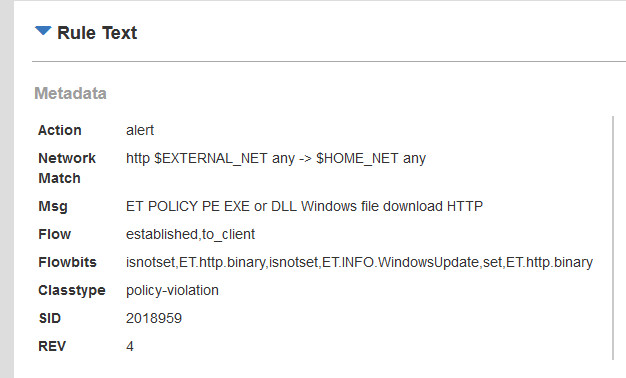
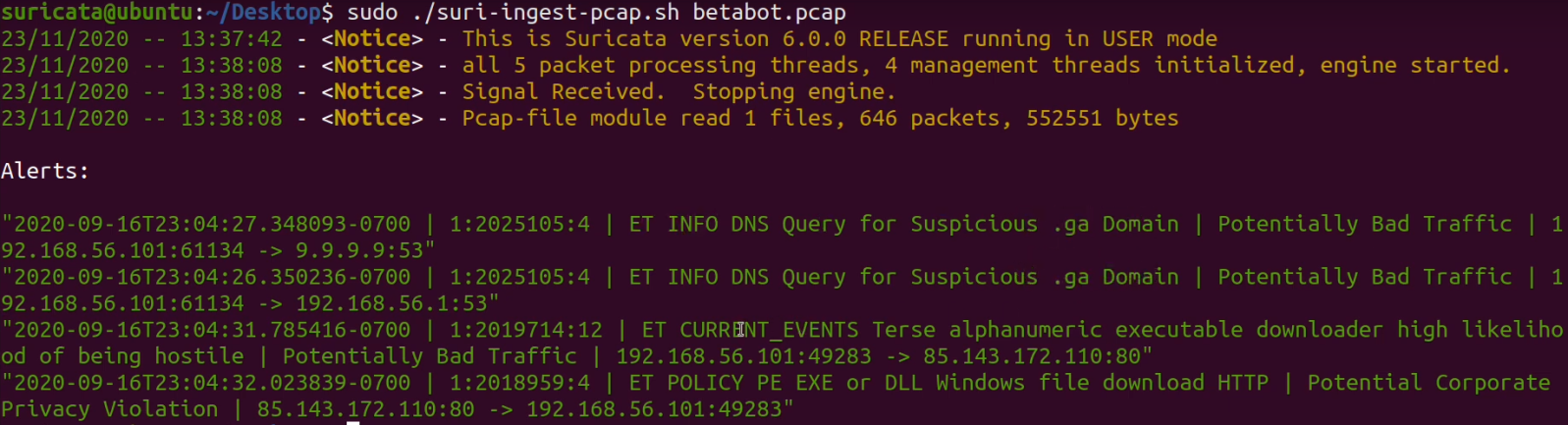
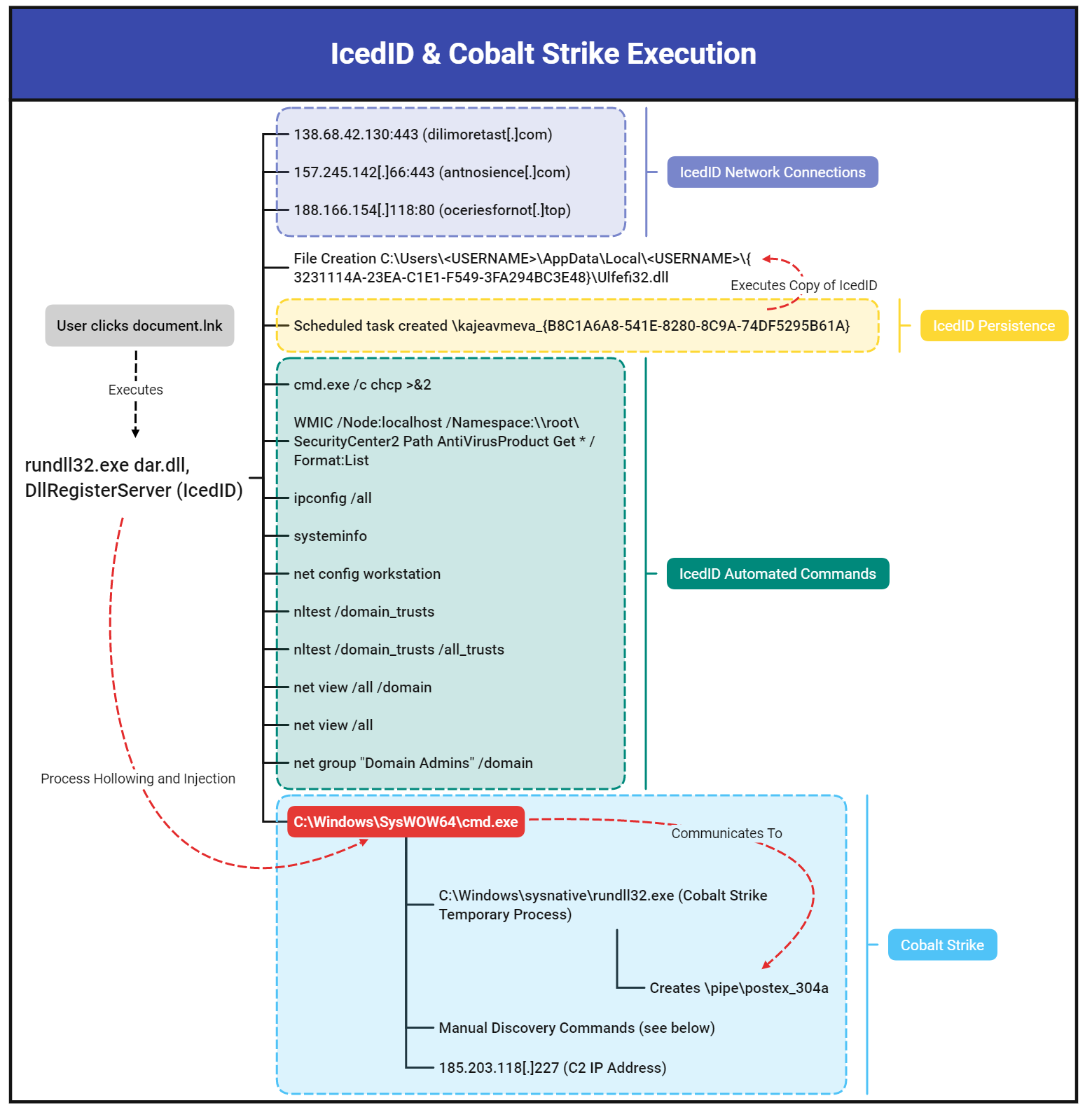
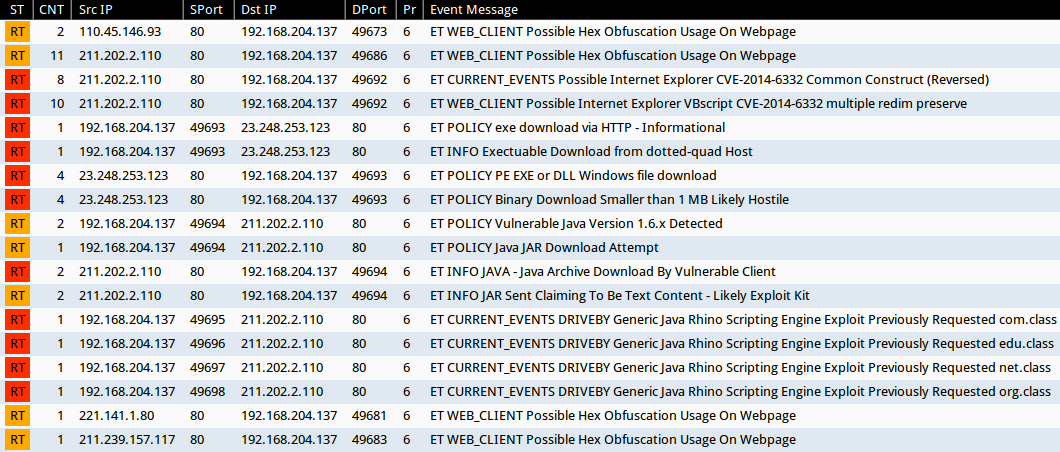
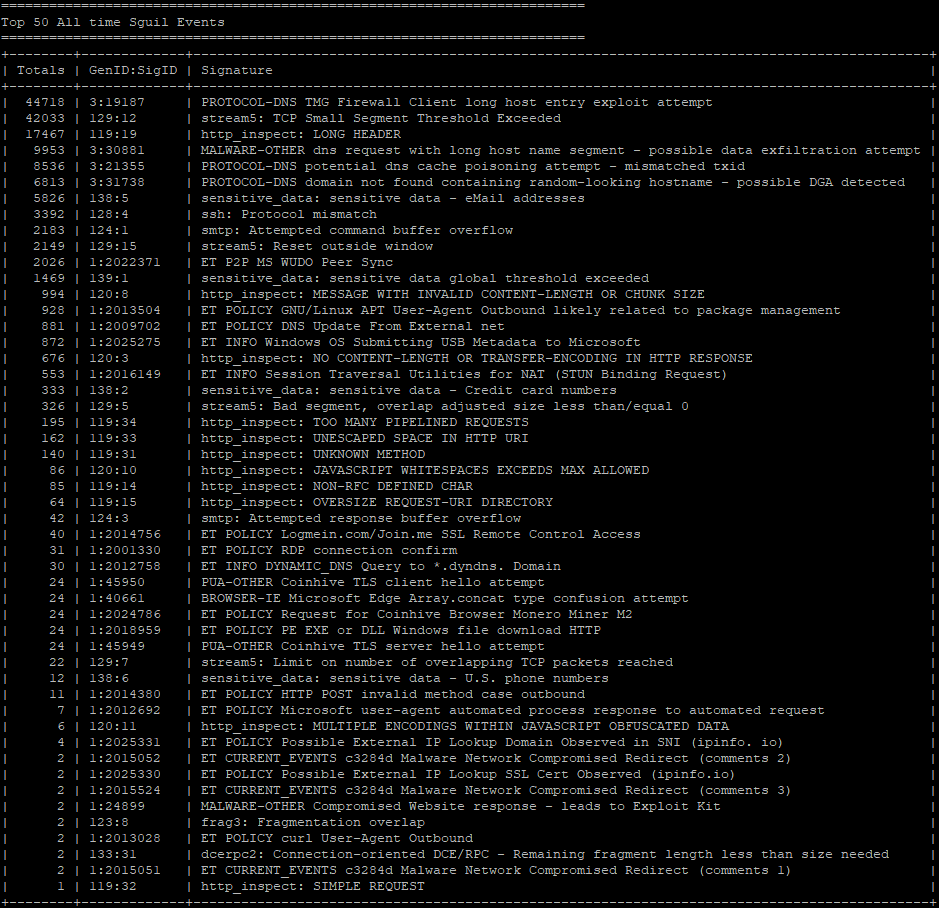
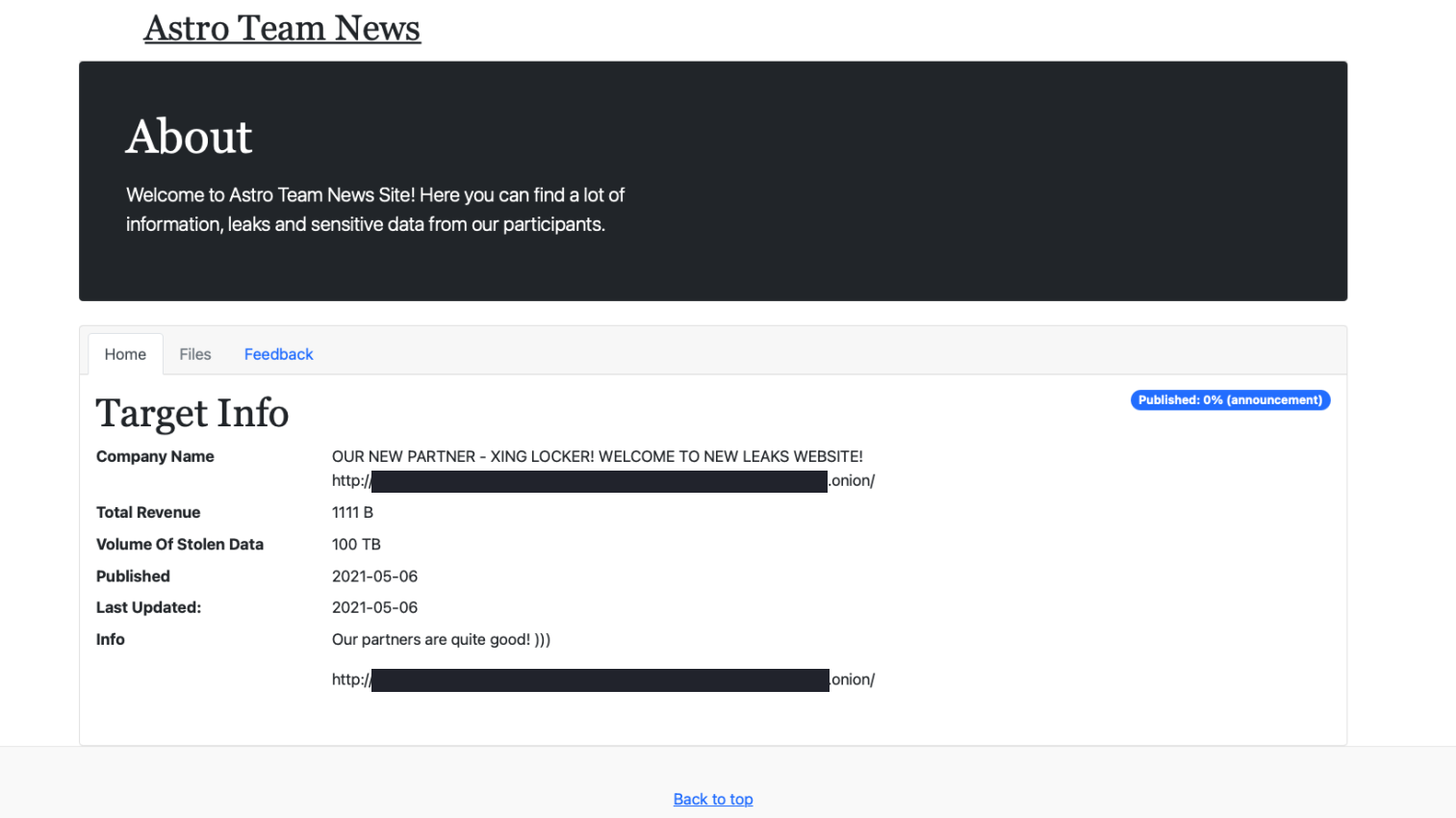
Security Onion - Linux Distro For Intrusion Detection, Network Security Monitoring, And Log Management

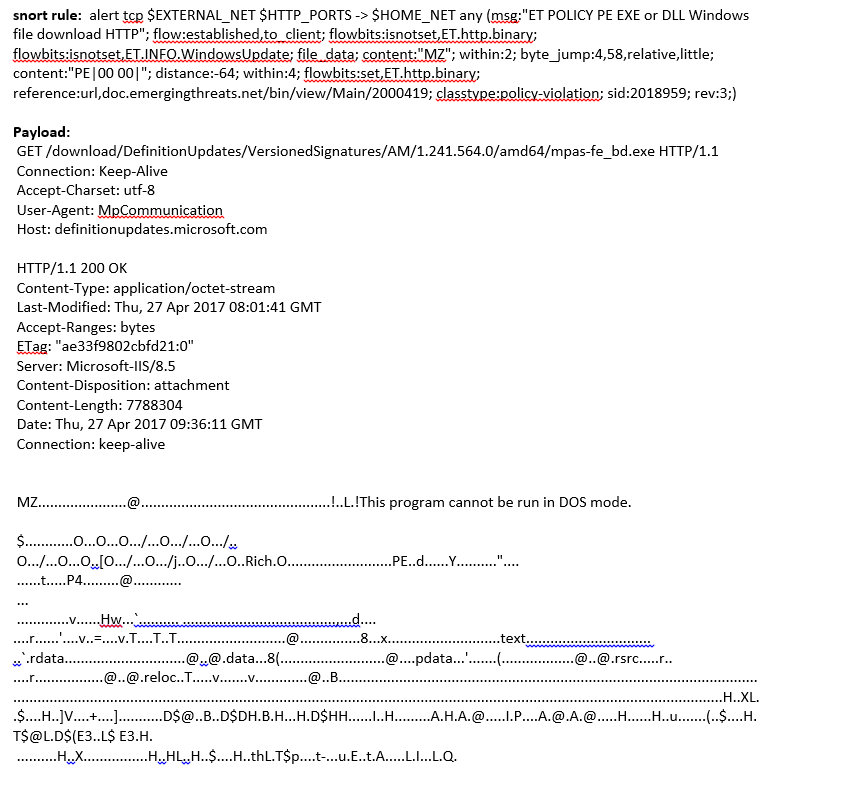
ids - intrusion prevention system detected "et policy pe exe" should i worry - Information Security Stack Exchange
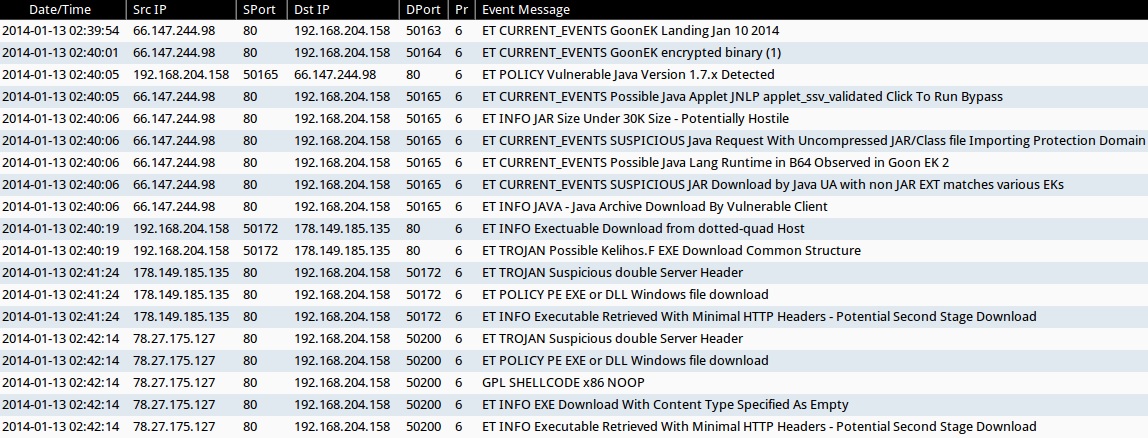
Sha256: 129569554b67a7be192a1a2bc5986337695b7676e347bb48473da4754ef479d7 - AlienVault - Open Threat Exchange

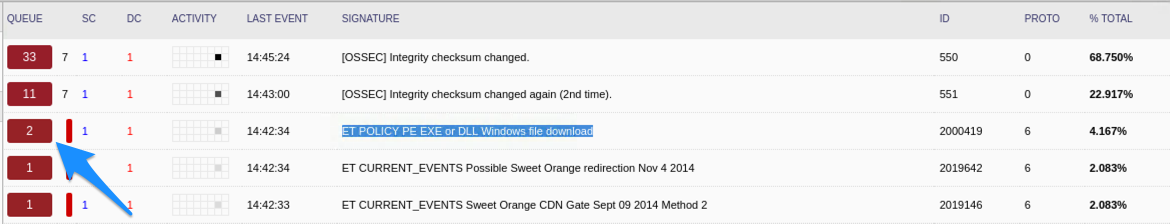
TryHackMe — Warzone 2 Write-up with Answers | 300 Points | by Karthikeyan Nagaraj | InfoSec Write-ups

Brad on Twitter: "2018-08-21 - more #malspam with password-protected Word docs, now pushing #Neutrino #malware - 1 email example, #pcap of associated traffic, and associated #malware samples at: https://t.co/cZzzwzJc3x - Until today,
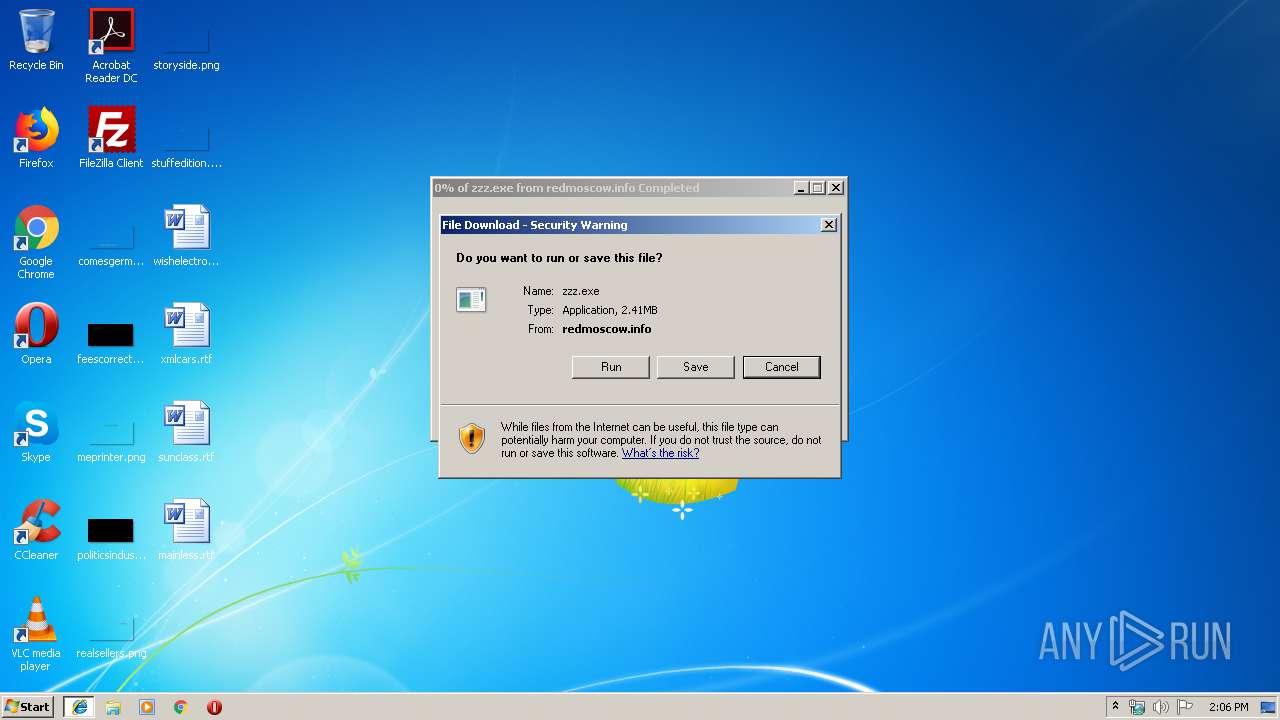
Malware analysis http://redmoscow.info/tmp/zzz.exe Malicious activity | ANY.RUN - Malware Sandbox Online